5 Cybersecurity Best Practices You Should Know

Below is a list of five of the more important cybersecurity best practices that you should be familiar with. When you take the time to fully adopt these practices, you can ensure that you’re putting yourself in the best position to minimise the possibility of an attack.
That said, it’s important that you adopt a fully comprehensive security plan – and not just depend on one thing. The information contained in this article is more of a starting point, for your cyber security efforts. Information you should adopt and expand upon, on your quest to utilising a full recovery and incident plan, and everything else that comes along with it. For a more robust approach, consider CISO training.

Connect To Secure Wi-Fi
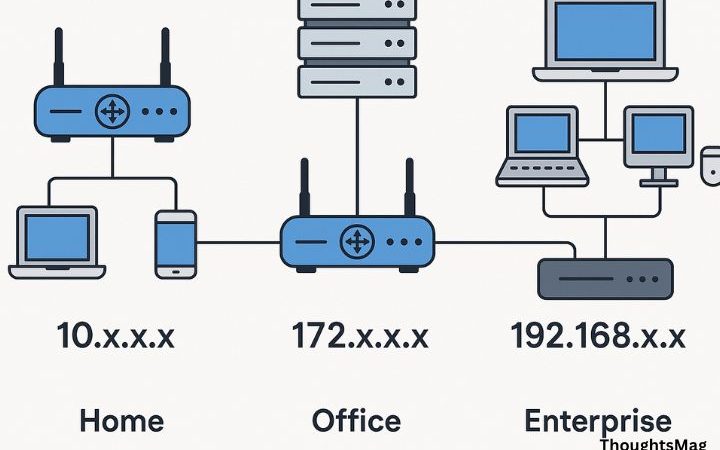
Any office Wi-Fi network must be encrypted, hidden (if possible) and secure. If you’re working from a remote location, then you should protect your data by using a VPN (virtual private network), if ones available to you. VPNs are extremely important when working away from office, such as when on business. The use of public Wi-Fi networks all comes with their risks, essentially making your data increasingly vulnerable to theft.
Secure Your Website
Almost websites run on HTTPS after Google’s initiative “HTTPS Everywhere”. If you are still behind then, it is time to install SSL certificate on your website. A website will have different requirement if it runs on a single domain or filled with lots of subdomains. For example, you can find cheap wildcard SSL certificate for unlimited subdomains’ security from reputed SSL providers. Wildcard SSL secures main domain along with different subdomains in a single certificate. Moreover, you will save your money with such certificate.
Wildcard SSL Certificate secures main domain along with different subdomains in a single certificate. Moreover, you will save your money with such certificate.
However, one thing you should be aware of, is that not all VPNs are made equally. If the company you work at, has its own VPN that it uses, then be sure to learn as much about it, as possible. There are tons of these services around, so I won’t go into any one of them. ut for your reference and knowledge, here’s the Top rated VPN today.
Back Up Your Data
Make sure you’re backing up your systems on a regular basis, irrespective of where the data on it is found. Whether it’s on a cloud-based server or a physical network. This is a practice you must adopt, which is why it should be included in your incident response plan. You want to store backups in a location separate from where your main data is stored.
If your network is attacked by cyber criminals, you may be forced to wipe a device or server. This is typically the case with ransomware viruses, which are increasingly more popular. If you store all your backups’ offline, and in many different locations, then it’ll make it next to impossible for infected systems to locate it. You want to carry out regular tests on your system, to ensure it’s inaccessible in the event of a breach. You also want to test your backups, just so you know, you can actually restore your data – in the event that any data has been compromised.
Use Different Passwords for Your Accounts
The obvious scenario is that it’s much easier to remember one complex password, than several of them. However, when you use the same password over and over again, in the event of a hack, it makes all your data vulnerable to possible infiltration.
Thus, as a workaround, it’s recommended that you use a password manager tool. These tools work by generating random complex passwords for all confidential services.
Additionally, if 2-step verification is something made available to you, by your ISP, then it’s definitely something you should invest in.
Install Security Updates
When you follow all best practices for IT security, it means keeping all your software, whether it be your browser, operating system or security tool, up to date. Antivirus tools are constantly being updated and improved to counter new threats, as and when they arrive.
If you receive a notification for a security update, it’s best practice to install it, as soon as possible. This also applies for any additional devices that you may use while at work. Updates are created to help your system defend against these new and constant threats.
Cybercriminals typically target your personal data. That’s why it’s important that you have a backup regiment in place. Rules, which include how and where your data is backed up, will likely have to be adopted.
Never Lose Your Device
So you’ve installed the latest internet security software on your smartphone and computer, and created new passwords to boot, implementing 2-step authentication. But, what happens if your smartphone or computer goes down? If you lose any of these devices, then you will lose all your personal files, emails, and photos in the process.
You do not want to find yourself in this possible. Which is why you should always have a password lock for your screen. You also may want to consider a bright coloured case for your phone, as this will decrease your chances of losing it, while regularly backing thingsup. In the event that you lose your phone, you may want to consider turning on the device location or third-party anti-theft application, so that it can help you in such instances. However, the best approach is always to be vigilant, so that you can nip the problem in the bud before it ever occurs.