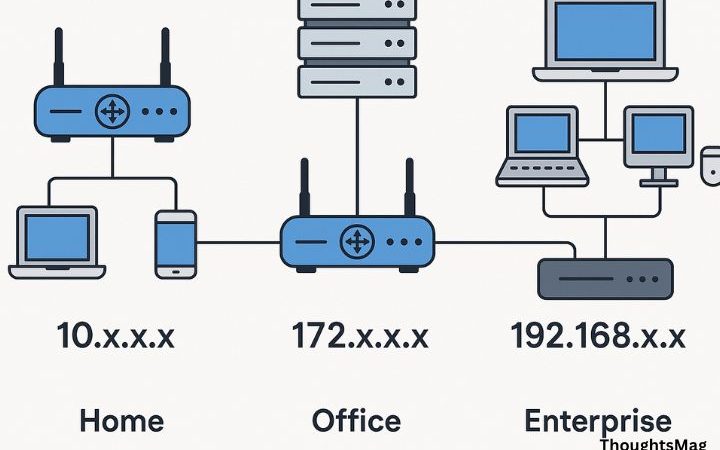
How to protect your personal information from data breaches?

It is very common for a virus to attack our computer. And normally, if you have proper protection, it is something that is solved without much problem. But, what if that virus results in a loss of your personal information and you don’t know where that data is going to end up? In that case, you will have suffered a security breach.
What is a data breach?
A data breach or security breach is “a security incident that affects personal data”, regardless of whether it is the consequence of an accident or an intentional action and whether it affects digital data or data on paper. In addition, these security breaches lead to the unauthorized destruction, loss, alteration, communication, or access of personal data.
Situations how these security breaches can occur are numerous, especially in the digital environment, and range from an unauthorized modification of the database, and the destruction of backup copies, to cyberattacks of different types whose objective is to access the personal data stored.
Types of data security breaches:
Although we can talk about different ways of causing a security breach, the truth is that when it comes to classifying them, there are three specific types depending on their objectives or consequences.
1. Confidentiality breach:
A breach of confidentiality occurs when there is unauthorized or non-legitimate access to the data storage platform or any part of it that may expose personal data.
2. Integrity breach:
The integrity breach refers to the manipulations or alterations of the original information stored in the system, producing a substitution of data that could cause some kind of damage.
3. Availability gap:
The availability breach refers to those attacks that cause the loss of access to the original data, either temporarily or permanently.
Research shows that human error is a leading cause of workplace safety incidents. Unfortunately, anyone who has poor information security habits at work is probably also putting their personal information at risk.
Security of your personal information should be an everyday task to reduce the risk of data breaches while protecting personal and confidential information inside and outside the workplace.
Here we give you the best practices to make a difference:
Ways to protect your personal information from data breaches:
Do not share confidential documents:
Don’t share sensitive data unless necessary. Before you share any sensitive information, find out why you need it and how it will be safeguarded. As for the online world, we must be more cautious and not share personal data on social networks and other platforms where unknown people can easily find it.
In addition, you must always set the privacy and security settings on web services and devices and when you send sensitive information by WhatsApp, message, or email, you must carefully review the senders and their needs. To find and verify any unknown people in your life, you can use Nuwber. Type the name of the person in question and see who they are.
Adjust the privacy settings of your social media profile:
Do you share your birthday on social media? And your middle name? Does your mom’s profile have her maiden name? Did you post that old photo of the first pet you found in the attic?
If the answer to any of these questions is ‘Yes’, you have a lot of work ahead of you. Public social media profiles are an open door for cybercriminals.
In countless cases, the information that people voluntarily share on Facebook and Instagram is enough to discover the answers to security questions. Or rebuild your identity to create new profiles on your behalf. To fix this vulnerability, be careful who can see your data. Adjust your settings for maximum privacy.
Beware of online and offline scams:
According to an analysis of data breaches in the US, hacking (phishing, ransomware, and skimming) was the primary attack method for 63% of overall breaches in the past year. You have to learn to recognize different frauds and consult only trusted websites, in addition to having continuous security training.
If you receive emails that require immediate action with misspellings or other errors, links, and attachments, be wary of them. In case of doubt and if you have not requested the information offered, delete them.
Enable encryption on all your devices:
Losing your phone, tablet or laptop is nothing short of a complete disaster. However, if your devices are easy to unlock and unencrypted, it’s a direct catastrophe.
Anyone who has them has a golden ticket to all your data and accounts. To prevent this from happening, make sure your devices have complex passwords and PINs to deny anyone easy access. And crucially, enable encryption.
On Apple devices, enable FileVault. On Android, make sure encryption is enabled in the “encryption and credentials” tab of the security menu. Encryption ensures that even if someone takes your device, they won’t be able to read any of the data on it.
Protect confidential information:
Keep all confidential information password protected. You must physically lock devices and use available IT locks, such as biometrics and security keys. Choose strong passwords (not the default or whatever is easy to guess) and don’t use the same one on different accounts.
Never leave computers, laptops, or other sensitive documents or devices visible in vehicles, or unattended in public places, where they can be stolen.
Be careful while using public Wi-Fi:
Be careful when using Wi-Fi in public places, as these networks are frequented by cybercriminals. Avoid sending sensitive data over this type of wi-fi, and if you don’t have a choice, use a controlled virtual private network (VPN). In addition, you must encrypt sensitive information sent over public networks (encryption software encrypts information sent over the internet).
Proper destruction:
It is vital to dispose of all sensitive information securely. The insecure disposal of hardware and paper continues to be a significant cause of security incidents. Find out which documents you should keep and for how long, and when no longer needed, destroy them securely. Don’t throw papers in the recycling bin or the garbage can either, shred them safely.
Hard drives should also be made “unreadable” before disposal, as information thieves can retrieve information from old computing devices and electronic media even if it was ‘deleted’.